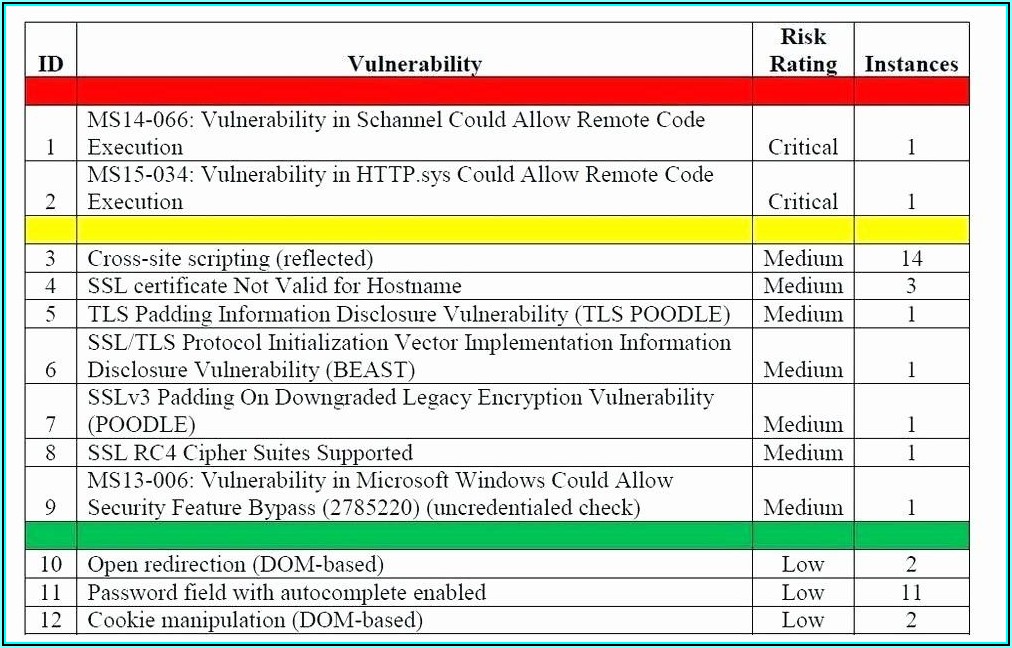
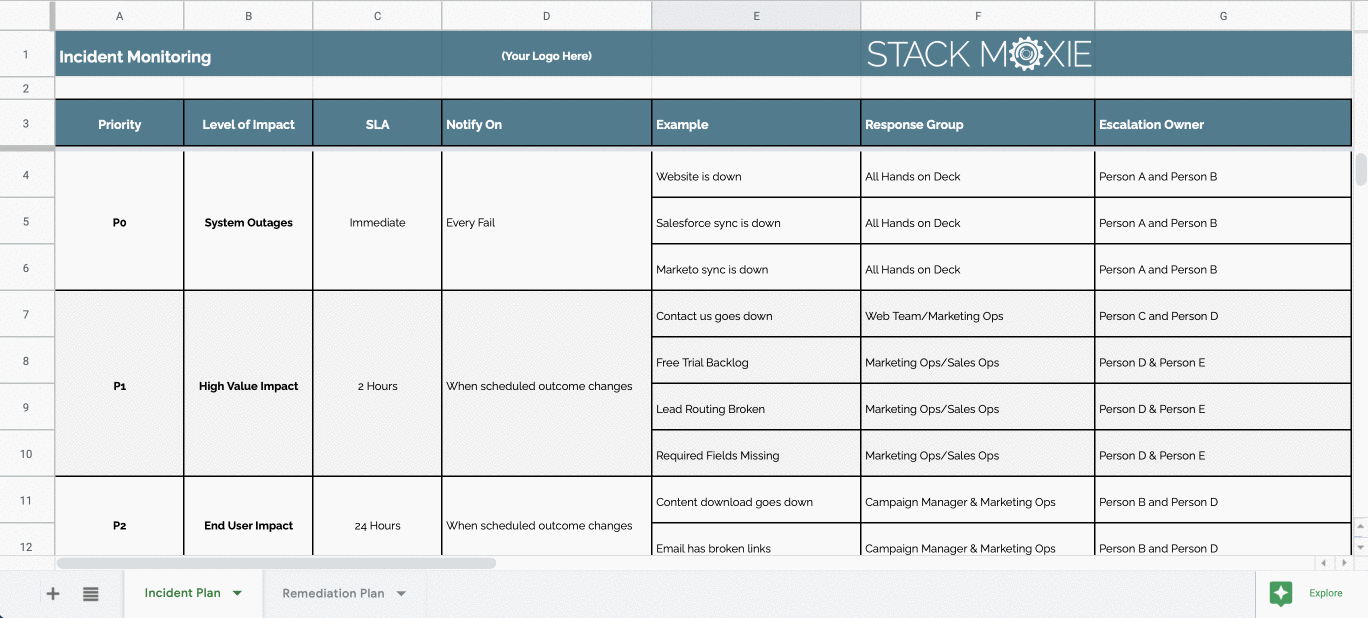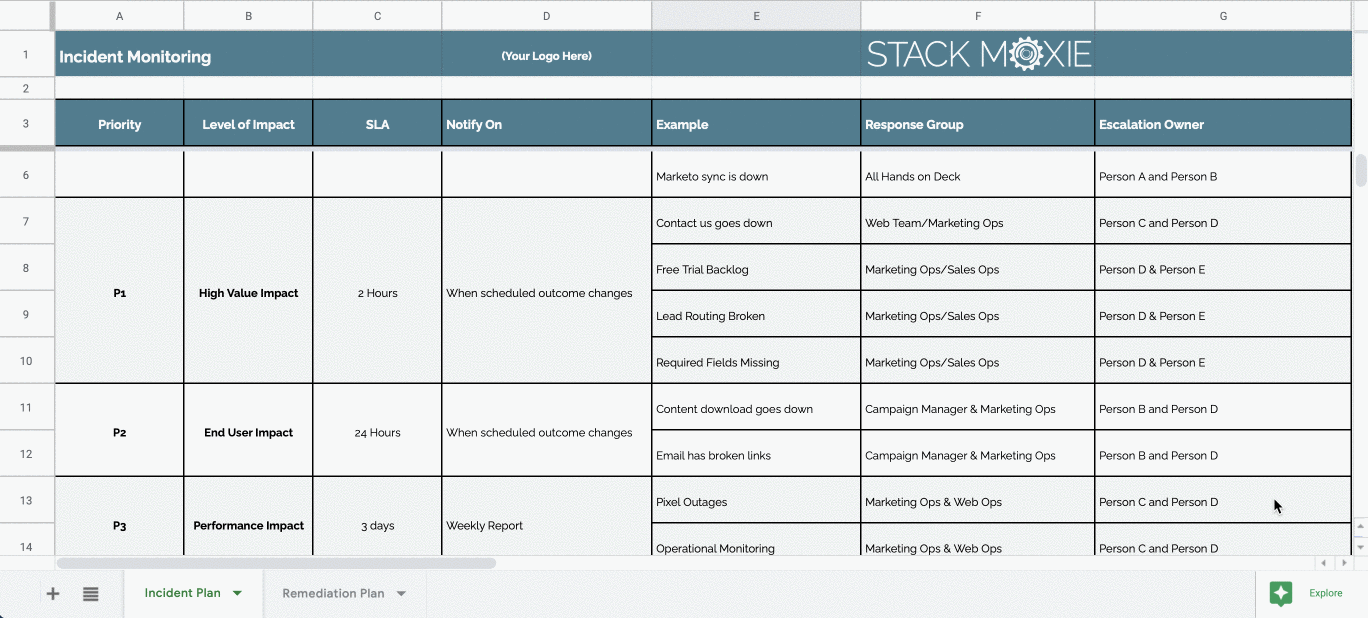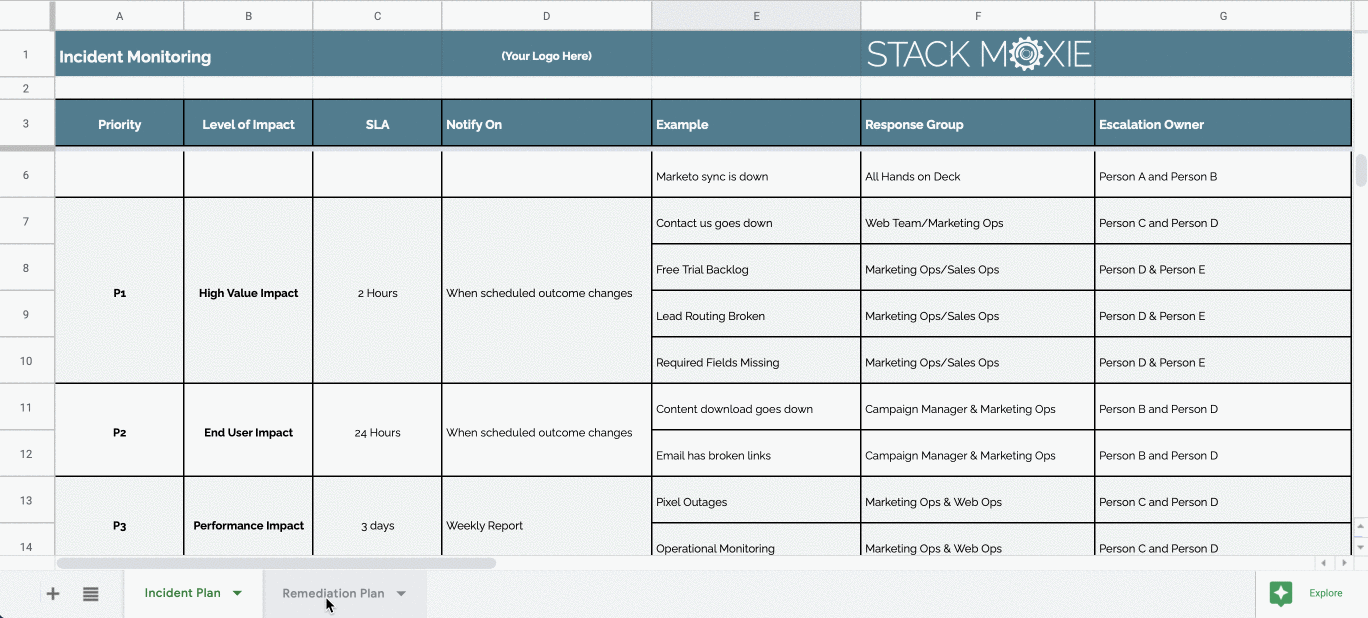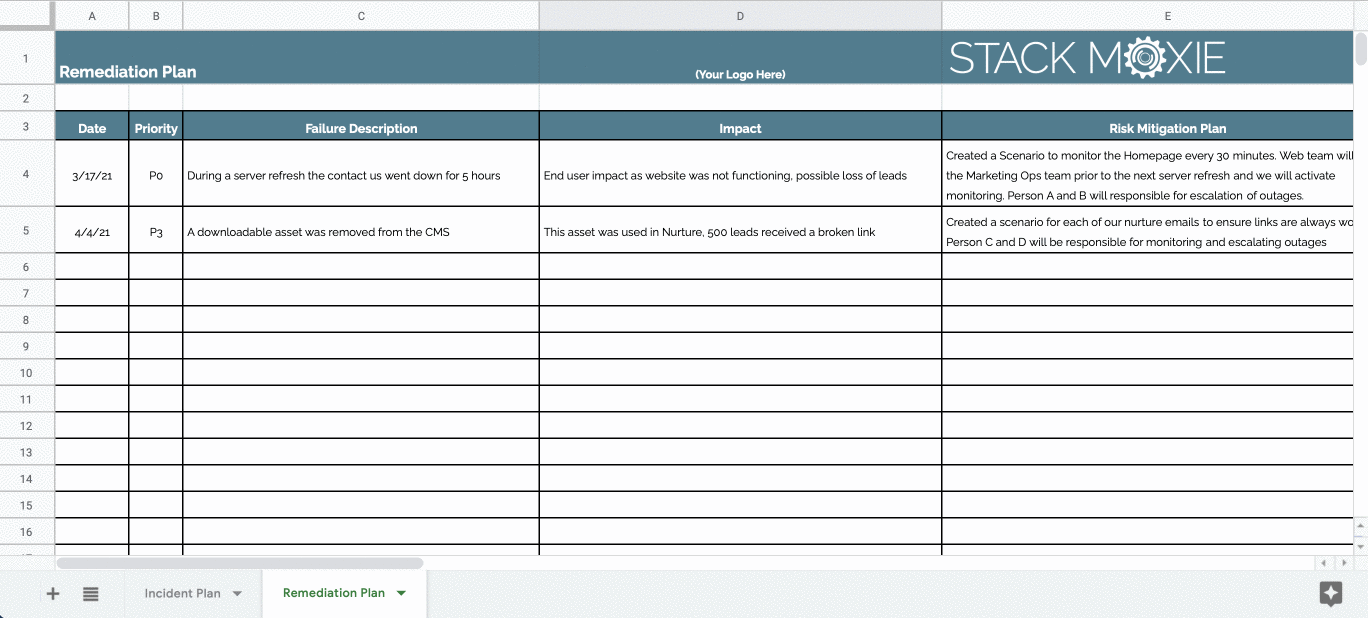
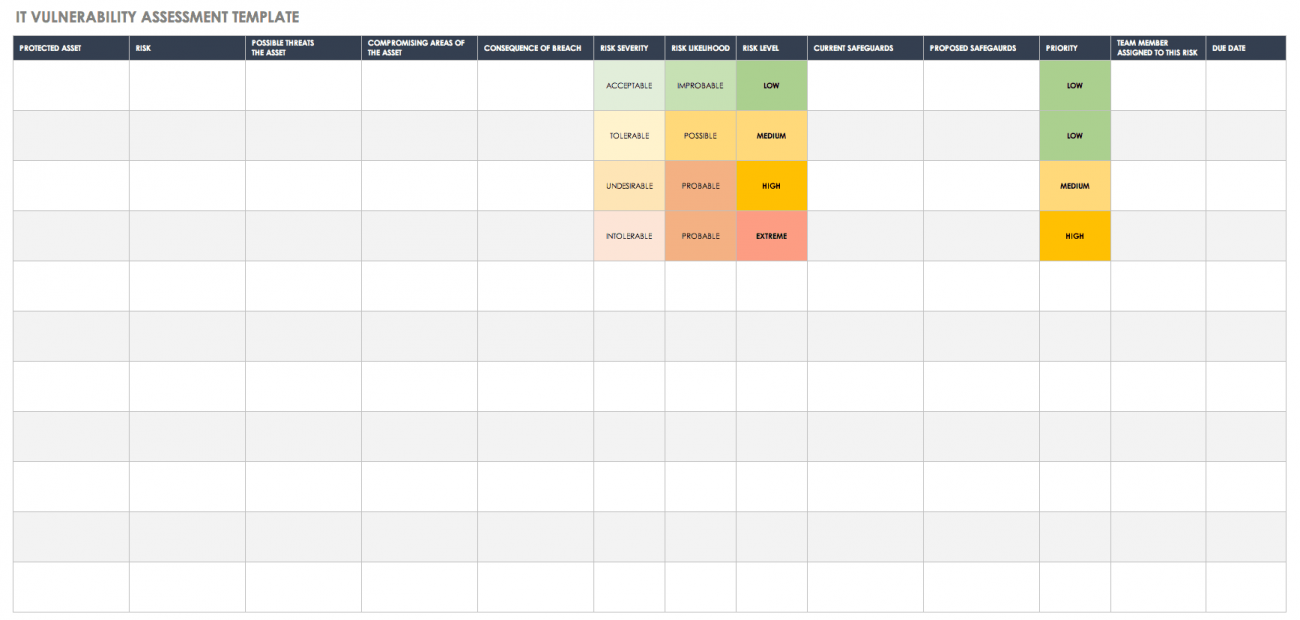
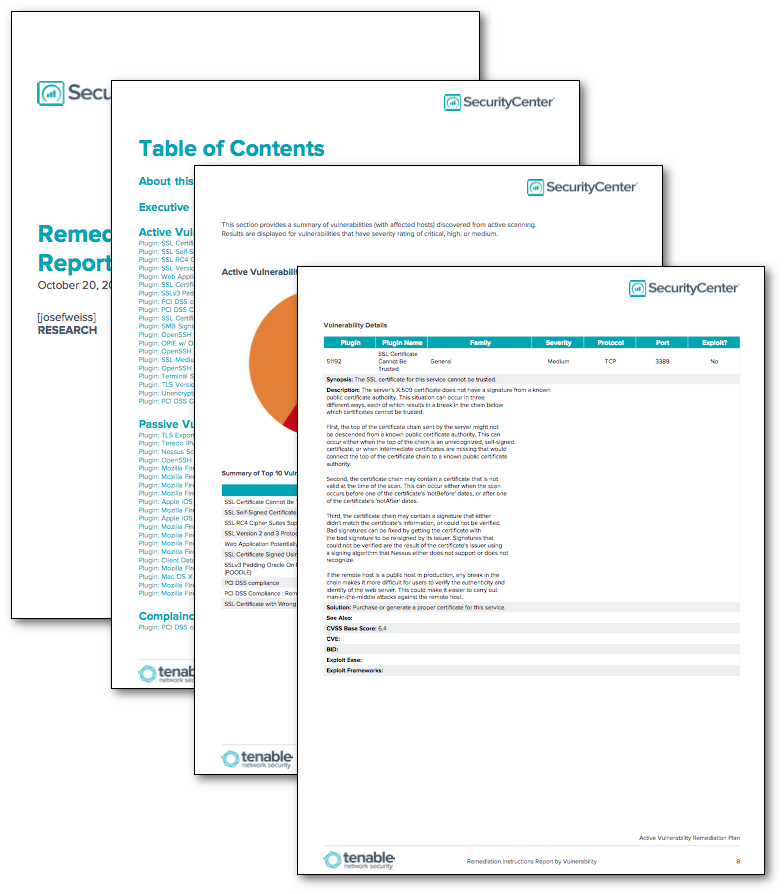
Vulnerability Remediation Plan Template - Web five tips for crafting a cybersecurity risk remediation plan: Web remediation of network vulnerabilities is something every organization wants done before hackers exploit the weaknesses. Web this policy template is meant to supplement the cis controls v8. Web the guide provides in depth coverage of the full vulnerability management lifecycle including the preparation phase, the vulnerability. Web active vulnerability remediation plan: Web the vulnerability remediation process is a workflow that fixes or neutralizes detected weaknesses including bugs and vulnerabilities. This chapter provides a top 20 summary of vulnerabilities. Web vulnerability remediation plan template client name date address line 1 address line 2 component weakness. Web for example, the task “scope” feeds into multiple processes: Web • developing a vulnerability analysis and resolution strategy • developing a vulnerability management plan •.
Vulnerability Remediation Plan Template Flyer Template
Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. Web the guide provides in depth coverage of the full vulnerability management lifecycle including the preparation phase, the vulnerability. Web dod vulnerability management originating component:office of the dod chief information officer. The policy statements included within this document can be used by all.
7 Security Assessment Samples Examples Templates Sample Templates
Web active vulnerability remediation plan: Web vulnerability patch management template custom tailored plan risk assessment project management weekly. The policy statements included within this document can be used by all cis implementation. Web the vulnerability remediation process is a workflow that fixes or neutralizes detected weaknesses including bugs and vulnerabilities. Web the remediation plan report template includes the following sections:
Incident & Remediation Plan Template for managing critical errors and
Web dod vulnerability management originating component:office of the dod chief information officer. Web for example, the task “scope” feeds into multiple processes: Web vulnerability remediation plan template client name date address line 1 address line 2 component weakness. Web 9+ risk remediation plan samples. Web the guide provides in depth coverage of the full vulnerability management lifecycle including the preparation.
Free Vulnerability Assessment Templates Smartsheet
Web this policy template is meant to supplement the cis controls v8. Web dod vulnerability management originating component:office of the dod chief information officer. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. Utilize centralized and continuous scanning. Web vulnerability remediation plan template client name date address line 1 address line 2.
Simplify Vulnerability Management with Nexpose 5.6
Web this policy template is meant to supplement the cis controls v8. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. Web the vulnerability risk remediation lifecycle can be summarized to include three stages: Web the vulnerability remediation process is a workflow that fixes or neutralizes detected weaknesses including bugs and vulnerabilities..
Free Vulnerability Assessment Templates Smartsheet
Web vulnerability patch management template custom tailored plan risk assessment project management weekly. This chapter provides a top 20 summary of vulnerabilities. Web 9+ risk remediation plan samples. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Web five tips for crafting a cybersecurity risk remediation.
Web this report provides detailed information on the top discovered vulnerabilities, and contains steps to. Web remediation of network vulnerabilities is something every organization wants done before hackers exploit the weaknesses. Web active vulnerability remediation plan: Web five tips for crafting a cybersecurity risk remediation plan: Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets.
30 Security assessment Plan Template Security assessment, Business
Web this report provides detailed information on the top discovered vulnerabilities, and contains steps to. Web the remediation plan report template includes the following sections: The policy statements included within this document can be used by all cis implementation. Web five tips for crafting a cybersecurity risk remediation plan: Web the vulnerability remediation process is a workflow that fixes or.
ICVulnerabilityRemediationPlanTemplate_Google.xltx Google Sheets
Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Web the vulnerability remediation process is a workflow that fixes or neutralizes detected weaknesses including bugs and vulnerabilities. Web in order to respond to product security incident, vulnerabilities, and patches immediate and permanent remediation. Web this policy.
Vulnerability Remediation Process Ppt Powerpoint Presentation Objects
Web the remediation plan report template includes the following sections: Web in order to respond to product security incident, vulnerabilities, and patches immediate and permanent remediation. Web the guide provides in depth coverage of the full vulnerability management lifecycle including the preparation phase, the vulnerability. This chapter provides a top 20 summary of vulnerabilities. Web vulnerability patch management template custom.
Web the remediation plan report template includes the following sections: Web this report provides detailed information on the top discovered vulnerabilities, and contains steps to. Web • developing a vulnerability analysis and resolution strategy • developing a vulnerability management plan •. The policy statements included within this document can be used by all cis implementation. Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Web for example, the task “scope” feeds into multiple processes: Web in order to respond to product security incident, vulnerabilities, and patches immediate and permanent remediation. Web vulnerability patch management template custom tailored plan risk assessment project management weekly. Web 9+ risk remediation plan samples. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks,. This chapter provides a top 20 summary of vulnerabilities. Web the guide provides in depth coverage of the full vulnerability management lifecycle including the preparation phase, the vulnerability. Web dod vulnerability management originating component:office of the dod chief information officer. Finding vulnerabilities through scanning and testing, prioritising , fixing, and monitoring vulnerabilities. Web this policy template is meant to supplement the cis controls v8. Web active vulnerability remediation plan: Web five tips for crafting a cybersecurity risk remediation plan: Web the vulnerability remediation process is a workflow that fixes or neutralizes detected weaknesses including bugs and vulnerabilities. Web the vulnerability risk remediation lifecycle can be summarized to include three stages: Utilize centralized and continuous scanning.
Web Active Vulnerability Remediation Plan:
Web five tips for crafting a cybersecurity risk remediation plan: Web this report provides detailed information on the top discovered vulnerabilities, and contains steps to. Utilize centralized and continuous scanning. Web vulnerability patch management template custom tailored plan risk assessment project management weekly.
Web The Vulnerability Risk Remediation Lifecycle Can Be Summarized To Include Three Stages:
Web the remediation plan report template includes the following sections: Web develop a plan to continuously assess and track vulnerabilities on all enterprise assets within the enterprise’s infrastructure, in order to remediate, and. Web dod vulnerability management originating component:office of the dod chief information officer. This chapter provides a top 20 summary of vulnerabilities.
Web 9+ Risk Remediation Plan Samples.
Web the vulnerability remediation process is a workflow that fixes or neutralizes detected weaknesses including bugs and vulnerabilities. Finding vulnerabilities through scanning and testing, prioritising , fixing, and monitoring vulnerabilities. Web this policy template is meant to supplement the cis controls v8. Web • developing a vulnerability analysis and resolution strategy • developing a vulnerability management plan •.
Web Vulnerability Management Is A Continuous, Proactive, And Often Automated Process That Keeps Your Computer Systems, Networks,.
Web in order to respond to product security incident, vulnerabilities, and patches immediate and permanent remediation. Web for example, the task “scope” feeds into multiple processes: Web remediation of network vulnerabilities is something every organization wants done before hackers exploit the weaknesses. Web vulnerability remediation plan template client name date address line 1 address line 2 component weakness.