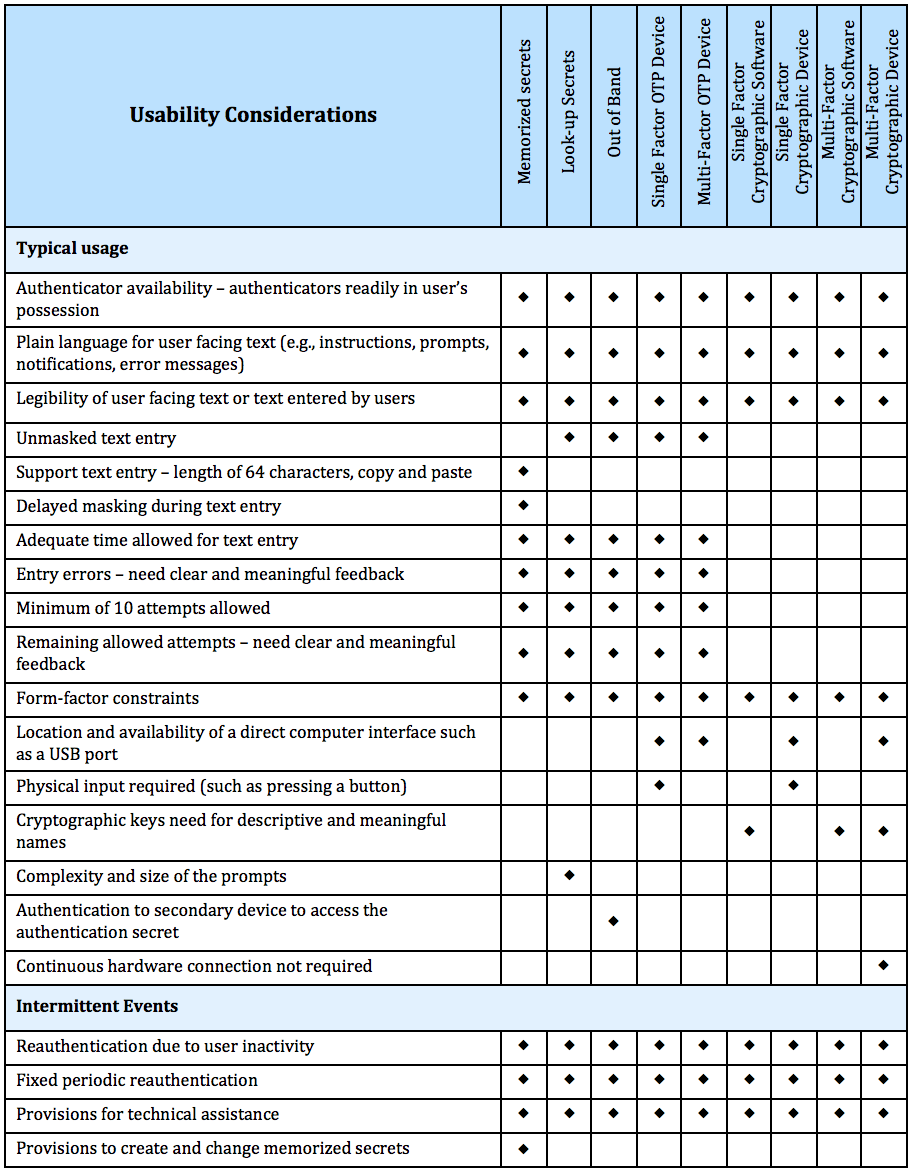
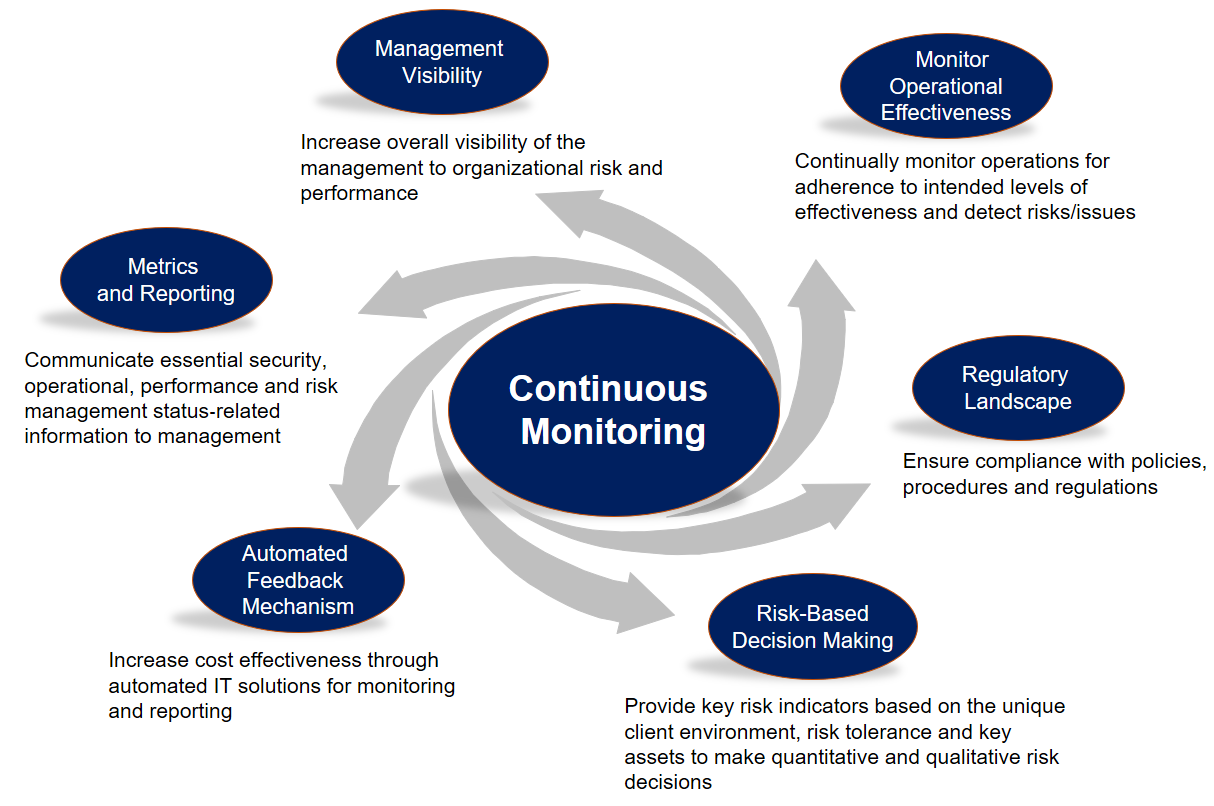
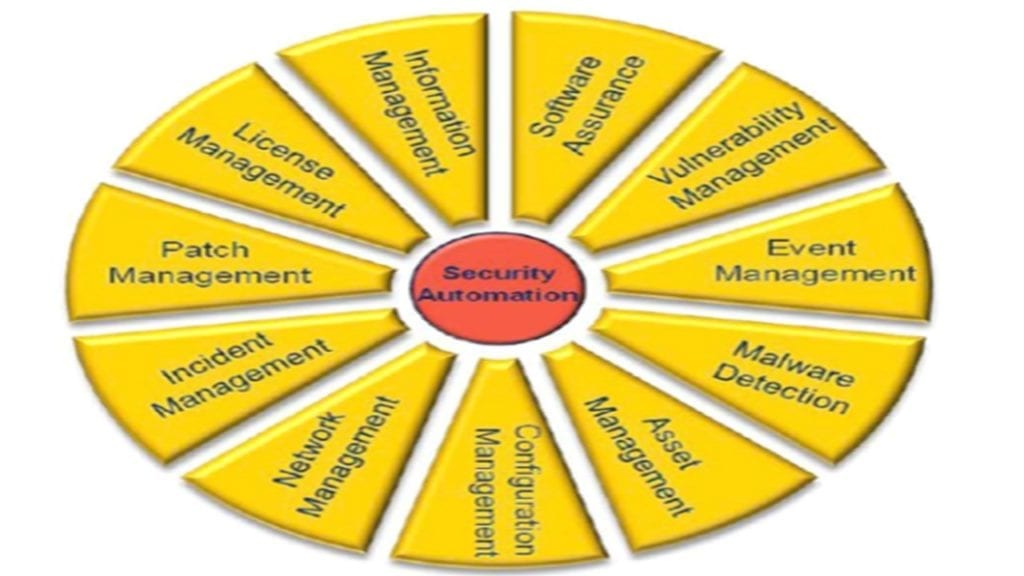
Nist Continuous Monitoring Plan Template - Web as defined by nist, the process for continuous monitoring includes the following initiatives: § define a continuous monitoring strategy based on risk tolerance that maintains clear visibility into assets. Web abstract the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program providing. This publication describes an example methodology for assessing an organization's information security continuous monitoring (iscm) program. Web new new new and after we build it right. Web nistir 8212, an information security continuous monitoring program assessment, provides an operational approach to the assessment of an organization’s iscm program using. It was developed directly from.
Cyber Security and Cyber Liability Protection IT Support Managed
It was developed directly from. Web as defined by nist, the process for continuous monitoring includes the following initiatives: Web new new new and after we build it right. Web abstract the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program providing. Web nistir 8212,.
Nist Risk Management Framework Template Cybersecurity framework
This publication describes an example methodology for assessing an organization's information security continuous monitoring (iscm) program. § define a continuous monitoring strategy based on risk tolerance that maintains clear visibility into assets. Web nistir 8212, an information security continuous monitoring program assessment, provides an operational approach to the assessment of an organization’s iscm program using. Web as defined by nist,.
Nist 800 53 Controls Spreadsheet Xls —
Web abstract the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program providing. This publication describes an example methodology for assessing an organization's information security continuous monitoring (iscm) program. Web new new new and after we build it right. Web as defined by nist, the.
Monitoring & IT Security CAPZEN TECHNOLOGIES
This publication describes an example methodology for assessing an organization's information security continuous monitoring (iscm) program. It was developed directly from. Web nistir 8212, an information security continuous monitoring program assessment, provides an operational approach to the assessment of an organization’s iscm program using. Web as defined by nist, the process for continuous monitoring includes the following initiatives: § define.
Information Security Continuous Monitoring (ISCM) YouTube
§ define a continuous monitoring strategy based on risk tolerance that maintains clear visibility into assets. Web abstract the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program providing. Web as defined by nist, the process for continuous monitoring includes the following initiatives: Web nistir.
Rmf Continuous Monitoring Plan Template Master of Documents
Web nistir 8212, an information security continuous monitoring program assessment, provides an operational approach to the assessment of an organization’s iscm program using. Web new new new and after we build it right. It was developed directly from. § define a continuous monitoring strategy based on risk tolerance that maintains clear visibility into assets. Web abstract the purpose of this.
NIST SP 800137 Information security continuous monitoring (ISCM)
Web abstract the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program providing. § define a continuous monitoring strategy based on risk tolerance that maintains clear visibility into assets. Web as defined by nist, the process for continuous monitoring includes the following initiatives: Web new.
TEMPLATE Continuous Monitoring Plan (ConMon) ⋆ The Cyber Sentinel
It was developed directly from. Web abstract the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program providing. This publication describes an example methodology for assessing an organization's information security continuous monitoring (iscm) program. Web nistir 8212, an information security continuous monitoring program assessment, provides.
Nist 800 Risk Assessment Template Information System Sensitivity
It was developed directly from. Web new new new and after we build it right. Web abstract the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program providing. Web nistir 8212, an information security continuous monitoring program assessment, provides an operational approach to the assessment.
NIST Revises Guide on Security Controls Security assessment, Business
Web new new new and after we build it right. Web nistir 8212, an information security continuous monitoring program assessment, provides an operational approach to the assessment of an organization’s iscm program using. § define a continuous monitoring strategy based on risk tolerance that maintains clear visibility into assets. Web abstract the purpose of this guideline is to assist organizations.
Web nistir 8212, an information security continuous monitoring program assessment, provides an operational approach to the assessment of an organization’s iscm program using. It was developed directly from. This publication describes an example methodology for assessing an organization's information security continuous monitoring (iscm) program. Web abstract the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program providing. Web as defined by nist, the process for continuous monitoring includes the following initiatives: Web new new new and after we build it right. § define a continuous monitoring strategy based on risk tolerance that maintains clear visibility into assets.
It Was Developed Directly From.
Web abstract the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program providing. Web nistir 8212, an information security continuous monitoring program assessment, provides an operational approach to the assessment of an organization’s iscm program using. § define a continuous monitoring strategy based on risk tolerance that maintains clear visibility into assets. Web new new new and after we build it right.
Web As Defined By Nist, The Process For Continuous Monitoring Includes The Following Initiatives:
This publication describes an example methodology for assessing an organization's information security continuous monitoring (iscm) program.